
It is common knowledge that the computer world is under constant threat of security breaches. Furthermore, cyber attacks are becoming more dangerous by the day. Over three trillion dollars are wasted every year owing to cyber crimes. And this huge wastage of money is likely to double by 2021. In a time where the number of internet users is increasing exponentially, it seems surreal to expect that threats can be completely eradicated.
Among a plethora of threats, the most infamous one is DDoS, which stands for distributed denial of service attack. In this malicious form of attack, normal traffic for the targeted server, network or service is disrupted by flooding it and its neighboring infrastructure with tremendous internet traffic. This new evil in cyber security has wreaked havoc with business processes.
The tech ecosystem is becoming increasingly dominated by machine learning. ML techniques provide a new approach to eradicate DDoS attacks. In this blog, we discuss a newly researched ML technique that helps restrain DDoS attacks.
SIP and VoIP
A team of researchers from University of Aegean, Greece, headed by Z Tsiatsikas, has published a study about tackling DDoS with machine learning in SIP-based VoIP systems. The popularity of VoIP systems in hardware ecosystems is the primary reason for choosing it for this study. In this age of internet, VoIP is the common choice for voice as well as multimedia communications.
Session Initiation Protocol (SIP) is the preference for initiating VoIP sessions. The basic structure of SIP/VoIP architecture has been described below:
User Agent (UA): This represents the endpoints of SIP, which are active units of the session. For example, in the case of voice communication, the caller and receiver represent endpoints for the session.
SIP Proxy Server: This entity acts both as client and server during the session. The tasks of the server are:
- Maintaining send and receive requests
- Transferring information between users
Registrar: Authentication processes and requests to register for UA are managed by this entity.
The VoIP provider keeps a record of the SIP communication. This is an important step as it gives out information to service providers regarding billing and accounting based activities of users. In addition to this essential data, it may also give out data about intrusion or dubious activities happening in a network. Hence, it is very important to monitor this area. If neglected, it may turn into a hotbed for DDoS attacks.
Combining ML Methods in VoIP
The researchers have employed these five standard ML algorithms in experiments:
- Sequential minimal optimization
- Neural networks
- Naïve Bayes
- Random Forest
- Decision trees
In the experiment, communications are taken care of through these algorithms. The network is made anonymous using HMAC (keyed-hash method authentication code) and classification features are created. These algorithms are tested using 15 different DDoS attack situations. This is done using a ‘test bed’ of DDoS simulations. The design, as done by researchers, is shown below:
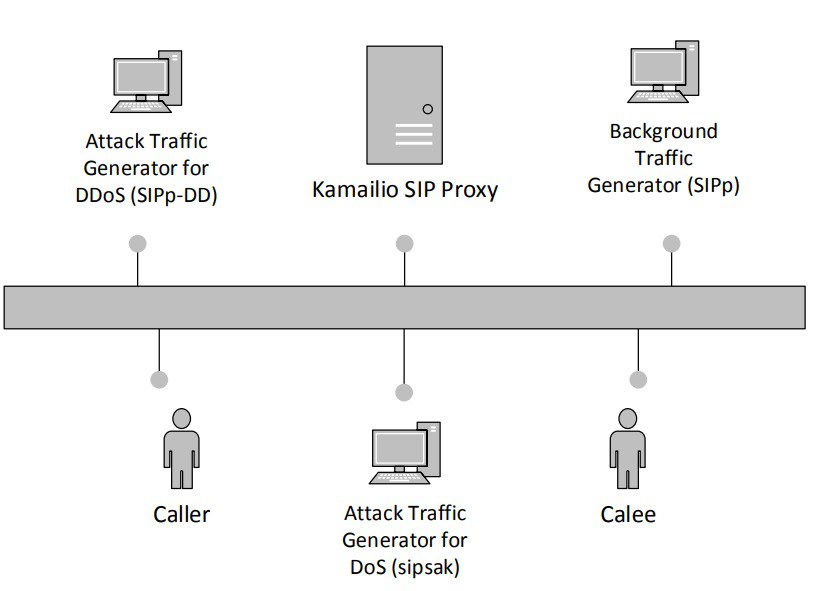
Image source: Analytics India
Following are some of the parameters of the experiment:
- 3 to 4 types of Virtual Machines (VMs) have been used for SIP proxy, legitimate users, and for generating attack traffic based on the scenario.
- Particularly for SIP proxy, popular VoIP server Kamailo (kam, 2014) has been employed.
- sipp v.3.21 and sipsak2 tools have been employed to simulate patterns for legitimate and DoS attack traffic.
- For simulation of DDoS attack, SIPpDD tool has also been used
- Weka tool has been used for machine learning analysis.
Performance
Compared to non-ML detection, these algorithms perform well. Speaking from an intrusion detection viewpoint, Random Forest and decision trees work best. With the rise in attack traffic, there’s drop in the rate of intrusion detection, which signifies the presence of DDoS.
To conclude, it can be said that machine learning surpass traditional methods of detecting attacks. This latest development in cyber security is another example of the rapid progress that machine learning is bringing into every field.
Interested in joining machine learning courses in Delhi? Wait not. Contact DexLab Analytics Right Now and get yourself enrolled for the best machine learning training in Delhi.
This article has been sourced from: www.analyticsindiamag.com/machine-learning-chasing-out-ddos-cyber-security
Interested in a career in Data Analyst?
To learn more about Data Analyst with Advanced excel course – Enrol Now.
To learn more about Data Analyst with R Course – Enrol Now.
To learn more about Big Data Course – Enrol Now.To learn more about Machine Learning Using Python and Spark – Enrol Now.
To learn more about Data Analyst with SAS Course – Enrol Now.
To learn more about Data Analyst with Apache Spark Course – Enrol Now.
To learn more about Data Analyst with Market Risk Analytics and Modelling Course – Enrol Now.